QUESTION 41
Your network consists of one Active Directory domain. Your company has an intranet. You deploy Terminal Services terminal servers that run Windows Server 2008. You plan to make applications available to users on the intranet. You need to recommend a solution to ensure that each user session receives an equal share of the CPU resources on the terminal servers. What should you recommend?
A. Install and configure the Network Load Balancing feature on all terminal servers.
B. Install and configure the Terminal Services server role with the Terminal Services Session Broker
(TS Session Broker) services role on all terminal servers.
C. Install the Windows System Resource Manager (WSRM) feature on all terminal servers.
Set the resource-allocation policy.
D. Install the Network Policy and Access Services (NPAS) server role on another server.
Define and apply a new policy by using Network Policy Server (NPS).
Answer: C
Explanation:
To ensure that each user session receives an equal share of the CPU resources on the terminal servers, you need to install the Windows System Resource Manager (WSRM) feature on all terminal servers and configure a resource-allocation policy. Windows System Resource Manager (WSRM) on Windows Server 2008 allows you to control how CPU and memory resources are allocated to applications, services, and processes on the computer. WSRM uses resource-allocation policies to determine how computer resources, such as CPU and memory, are allocated to processes running on the computer. Network Load Balancing and TS Session Load Balancing allows you to balance client requests and use sessions load but not allow you to control the CPU and memory resources allocated to applications on a Terminal server. Network Policy Server allows you to configure health policies for network access and therefore cannot be used here.
Reference: Terminal Services and Windows System Resource Manager http://technet2.microsoft.com/windowsserver2008/en/library/36edff58-463f-466e-9c9b-cd7b82422d3c1033.mspx?mfr=true
QUESTION 42
Your company has two main offices located in two countries and multiple branch offices in each country. The wide area network (WAN) link between the offices has restricted and limited connectivity. The network consists of two Active Directory forests. The functional level of the forests is Windows 2000 Server. Each forest includes a root domain and four child domains. All resources for each forest are located only in a single country. You plan to deploy Active Directory Domain Services (AD DS). The AD DS deployment must support the following requirements:
– Replication traffic between the main offices must be minimized.
– Users in all offices must be able to access resources in all other offices.
– The solution must use the minimum amount of domains.
Which migration strategy should you recommend?
A. Restructure to a two-domain, two-forest Active Directory structure.
B. Restructure to a single-domain, single-forest Active Directory structure.
C. Restructure to a multi-domain, single-forest Active Directory structure.
D. Upgrade all existing domains and maintain the existing Active Directory structure.
Answer: A
Explanation:
To deploy Active Directory Domain Services (AD DS) and to make sure that the replication traffic between both the main offices are minimized and the users in all offices are able to access resources in all other offices, you need to modify the structure to deploy a two-domain, two-forest Active Directory structure. Usually a single forest is sufficient in many situations. However you need more than one forest if the network is distributed among many autonomous divisions as in this scenario, where two main offices are located in two different countries. Therefore you need two-forest Active Directory structure. You need to deploy two domain structures because you need to minimize the replication traffic between both the main offices. Replication traffic can be avoided by creating a separate domain for both the head office locations and not replicating that domain to the branch offices. In a forest containing a single domain, every object in the forest is replicated to every domain controller in the forest. This might lead to objects being replicated to places where they are rarely used, which is an inefficient use of bandwidth. For example, a user that always logs on at main office location does not need their user account replicated to a branch office location. Reference: Designing the Active Directory Structure / Physical partitioning http://209.85.175.104/search?q=cache:hiq_xR4u7rgJ:www.certmag.com/bookshelf/c09617945.pdf+ a+two-domain,+two-forest+Active+Directory+structure&hl=en&ct=clnk&cd=7&gl=in
QUESTION 43
Your network consists of two Active Directory forests. The Active Directory forests are configured as shown in the following table. (Click the Exhibit)
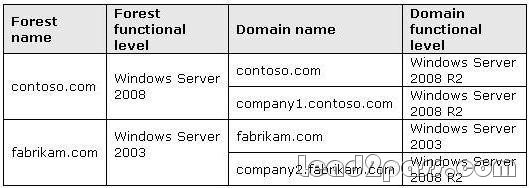
The contoso.com and fabrikam.com domains each contain one server that runs Active Directory Federation Services (AD FS). Users in the company1.contoso.com domain require access to an application server in the company2.fabrikam.com domain. The application server is configured to allow only Kerberos authentication. You need to ensure that users in the company1.contoso.com domain can access the application server in the company2.fabrikam.com domain. What should you do first?
A. Create a forest trust between the contoso.com forest and the fabrikam.com forest.
B. Create an external trust between the contoso.com domain and the fabrikam.com domain.
C. Create an AD FS federation trust between the contoso.com forest and the fabrikam.com forest.
D. Create an external trust between the company1.contoso.com domain and the company2.fabrikam.com domain.
Answer: A
QUESTION 44
Your company has a main office and a branch office. Your network consists of one Active Directory domain. All domain controllers run Windows Server 2008 R2. You need to plan the installation of a new server as a read-only domain controller (RODC) in the branch office. The plan must meet the following requirements:
– A branch office user must complete the RODC installation.
– The branch office user must only be a member of only the Domain Users security group.
What should you do first?
A. Create an installation media by using ntdsutil.
B. Instruct the user to join the new server to the domain.
C. Pre-create a read-only domain controller (RODC) account for the branch office server.
D. Create an organizational unit (OU) for the branch office. Delegate full control of the OU to the branch
office user.
Answer: C
Explanation:
To install a new server as a read-only domain controller (RODC) in the branch office and to ensure that the users of branch office must only be a member of the Domain Users security group, you need to Pre-create a read-only domain controller (RODC) account for the branch office server. When you pre-create the RODC account, you can delegate the installation and administration of the RODC to a user or better a security group.
Reference: Active Directory Domain Services: RODC (Read-Only Domain Controller) / Administrator Role Separation
http://trycatch.be/blogs/roggenk/archive/2007/08/01/active-directory-domain-services-rodc-read- only-domain-controller.aspx
QUESTION 45
Your network consists of one Active Directory forest. All servers run Windows Server 2008 R2. You plan to make multiple Web applications in the perimeter network accessible to external customers and partner company users. You need to design an access solution to meet the following requirements:
– Provide authentication and authorization for the external customers and partner company users. – Enable single sign-on (SSO) authentication so that users can access multiple Web applications from a single Web browser session.
What should you include in your design?
A. Deploy Network Policy and Access Services (NPAS).
B. Deploy Active Directory Rights Management Services (AD RMS).
C. Deploy Active Directory Lightweight Directory Services (AD LDS), and then deploy Active Directory
Federation Services (AD FS). ‘
D. Deploy Active Directory Lightweight Directory Services (AD LDS), and then configure AD FS Web
Agents on Internet Information Server (IIS) 7.0.
Answer: C
Explanation:
To implement single sign-on (SSO) authentication so that users can access multiple Web applications from a single Web browser session, you need to install Active Directory Federation Services (AD FS) on your Windows Server 2008 Server. You also need Active Directory Lightweight Directory Services (AD LDS) because AD FS requires at least one directory service: either Active Directory Domain Services (AD DS) or Active Directory Lightweight Directory Services (AD LDS) to implement single sign-on (SSO) authentication.
Reference: Windows Server 2008 Domain Services – Part 2: Active Directory Federation Services / How AD FS works
http://www.windowsnetworking.com/articles_tutorials/Windows-Server-2008-Domain-Services- Part2.html
QUESTION 46
Your network contains two servers named Server1 and Server2 that run Windows Server 2008. The servers have the Windows Server Hyper-V role installed. You plan to host six virtual machines on Server1 and Server2. You plan to enable host clustering on Server1 and Server2. Each virtual machine will use Pass-Through Disk Access. You need to recommend a storage configuration solution for Server1 and Server2 to support the planned virtual machines. What should you recommend?
A. Configure internal storage on Server1 to contain six RAID disk arrays.
Configure internal storage on Server2 to contain six RAID disk arrays.
B. Configure internal storage on Server1 to contain three RAID disk arrays.
Configure internal storage on Server2 to contain three RAID disk arrays.
C. Configure an iSCSI device to contain a logical unit number (LUN) mapped to one RAID array.
Configure Server1 and Server2 to connect to the iSCSI device.
D. Configure an iSCSI device to contain six logical unit numbers (LUN) mapped to six volumes on one
RAID array.
Configure Server1 and Server2 to connect to the iSCSI device.
Answer: D
Explanation:
To support the planned virtual machines for both the servers, you need to first Configure Server1 and Server2 to connect to the iSCSI device and then configure an iSCSI device to contain six logical unit numbers (LUN) mapped to six volumes on one RAID array. You must use SCSI if you need to expose more than 4 virtual disks to your guest. You must use IDE if your guest needs to boot to that virtual disk or if there are no Integration Components in the guest OS. You can also use both IDE and SCSI with the same guest.You can use iSCSI to expose disks directly to the guest (which is the term used for virtual machine) OS (without ever exposing it to the host). You need to configure an iSCSI device to contain six logical unit numbers (LUN) mapped to six volumes on one RAID array and not a logical unit number (LUN) mapped to one RAID array to modify the volume set capacity, RAID level and Stripe size.
Reference: Storage options for Windows Server 2008 Hyper-V / IDE or SCSI on the guest http://blogs.technet.com/josebda/archive/2008/02/14/storage-options-for-windows-server-2008-s- hyper-v.aspx
QUESTION 47
Your company has three offices. Each office is configured as an Active Directory site. The network consists of one Active directory domain. All domain controllers run Windows Server 2008 R2. The company has five departments. You use a domain-level Group Policy object (GPO) to install Microsoft Office on all client computers.
You need to deploy a GPO strategy to meet the following requirements:
– Install a custom application in one of the departments.
– Restrict access to removable storage devices for all users.
– Implement separate Windows Internet Explorer proxy settings for each physical location.
The strategy must maintain all settings applied by the existing GPOs.
What should you do?
A. Create a new group for each department. Create a new GPO for each site.
Create a new GPO for the domain and use the GPO to install the custom application.
B. Create a new organizational unit (OU) for each department.
Create a new GPO for each site and a new GPO for the domain.
Create a GPO for one department OU and use the GPO to install the application.
C. Create a new organizational unit (OU) for each department.
Create a single GPO for all the sites and a new GPO for the domain.
Create a single GPO for each department OU and use the GPO to install the custom application.
D. Create a new child domain for each department.
Create a new GPO for each site and a new GPO for each new child domain.
Create a single GPO for all the new child domains and use the GPO to install the custom application.
Answer: B
Explanation:
To install a custom application in one of the departments using GPO, you need to create a new organizational unit (OU) for each department and then create a GPO for that department OU and use that GPO to install the application. Next to restrict access to removable storage devices for all users you need to a new GPO for the domain and configure it to restrict access to removable storage devices for all users. You cannot use the already existing GPO because you want to maintain all settings applied by the existing GPOs. To implement separate IE proxy settings for each physical location, you need to create a new GPO for each site and use it to configure separate IE proxy settings for each physical location. Therefore, to accomplish the desired goal you need to, create a new organizational unit (OU) for each department, site, a new GPO for the domain, and a GPO for one department OU and use the GPO for the department OU to install the application
QUESTION 48
Your company has three offices. Each office contains servers that run Windows Server 2008 R2. The servers are configured as file servers. Users regularly travel between offices and require access to corporate data stored on their respective home servers. You need to plan a data access policy for the users. The solution must ensure that users can access corporate data from a local server when they are traveling. What should you include in your plan?
A. On all servers, install and configure Distributed File System (DFS).
B. On all servers, install and configure the File Server Resource Manager (FSRM) and the File Replication
Service (FRS).
C. On one server, install and configure the File Server Resource Manager (FSRM). On the other two servers,
install and configure the File Replication Service (FRS).
D. On one server, install and configure Distributed File System (DFS). On the other two servers, install and
configure the Background Intelligent Transfer Service (BITS).
Answer: A
Explanation:
To create a data access policy for the users that would ensure that users can access corporate data from a local server when they are traveling, you need to configure Distributed File System (DFS) on all the servers of the company. With DFS, you can make files distributed across multiple servers appear to users as if they reside in one place on the network. Users no longer need to know and specify the actual physical location of files in order to access them.
Reference: Why Use Microsoft DFS?
http://viewer.media.bitpipe.com/992544944_524/1206037959_795/Peer-Eguide_sWinIT.3.21fff.pdf
QUESTION 49
Your company has one main office and eight branch offices. Each branch office has 200 client computers and a local administrator. The network consists of one Active Directory domain. All domain controllers run Windows Server 2008 R2. You plan to deploy domain controllers to the branch office locations. You need to plan an administration solution for the branch offices that meets the following requirements:
– Branch office administrators must be able to update drivers on their respective branch office domain controllers.
– Branch office administrators must be able to log on only to domain controllers in their respective branches.
What should you include in your plan?
A. Deploy a Windows Server 2008 R2 read-only domain controller (RODC) in each branch office.
Assign the Administrators role for the RODC to the branch office administrators.
B. Deploy a Windows Server 2008 R2 read-only domain controller (RODC) in each branch office.
Assign the Network Configuration Operators role for the RODC to the branch office administrators.
C. Deploy a domain controller that runs a Server Core Installation of Windows Server 2008 R2 in each
branch office. Add the branch office administrator to the Server Operators domain local group.
D. Deploy a domain controller that runs a Server Core Installation of Windows Server 2008 R2 in each
branch office. Add the branch office administrator to the Administrators domain local group.
Answer: A
Explanation:
To install domain controllers in each branch office and to make sure that branch office administrators are allowed to log in only to the domain controllers of their branch and should be allowed to update drivers on the domain controllers of their branch, you need to deploy a Windows Server 2008 read-only domain controller (RODC) in each branch office and assign the Administrators role for the RODC to the branch office administrators. RODCs perform same as domain controllers except for the fact that they are more secure and read only. They allow users to log on to the domain and work best when the WAN link between branch offices and head office is unreliable and domain controllers cannot be contacted. RODCs provide Administrator Role Separation, which allows a local/regular domain user to be delegated local administrator privileges on a RODC, for the execution of regular maintenance work such as the install of software, updating drivers, troubleshooting connectivity issues, etc.
Reference: Windows Server 2008 Read Only Domain Controller RODC http://windowsis.com/blogs/windowsis/archive/2008/04/14/windows-server-2008-read-only- domain-controller-rodc.aspx
QUESTION 50
Your network contains one Active Directory forest that has a root domain and three child domains. All domain controllers run Windows Server 2003 Service Pack 1 (SP1). Each domain has a different password policy. The domain is configured as shown in the exhibit. (Click the Exhibit button.)
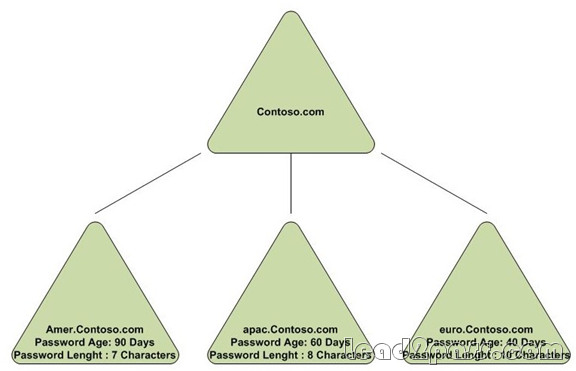
You plan to reduce the number of domains in the forest. You need to plan the restructuring of the forest to meet the following requirements:
– Maintain all existing password policies.
– Maintain all existing user account attributes.
What should you include in your plan?
A. Upgrade all domains to Windows Server 2008. Redirect the users container in the root domain by
using the redirusr.exe tool, and then remove the child domains. Enable fine-grained password policies.
B. Upgrade all domains to Windows Server 2008 and enable SID history. Move all user accounts from
the child domains to the root domain by using the movetree.exe tool, and then remove the child domains.
C. Upgrade the forest root domain to Windows Server 2008. Use the Active Directory Migration Tool
(ADMT) to migrate user accounts that contain SID history from the child domains to the forest root domain.
Remove the child domains.
D. Upgrade the forest root domain to Windows Server 2008. Use the Active Directory Migration Tool
(ADMT) to migrate user accounts from the child domains to the forest root domain, and then remove the
child domains. Enable fine-grained password policies.
Answer: D
Explanation:
To reduce the number of domains from the forest without loosing existing user account attributes and existing password policies, you need to Use the Active Directory Migration Tool (ADMT) to migrate user accounts that contain SID history from the child domains to the forest root domain.
Remove the child domains
SID history enables you to maintain user access to resources during the process of restructuring Active Directory domains. When you migrate an object to another domain, the object is assigned a new SID. Because you assign permissions to objects based on SIDs, when the SID changes, the user loses access to that resource until you can reassign permissions. When you use ADMT to migrate objects between domains, the SID history is automatically retained. In this way, the SID from the source domain remains as an attribute of the object after the object is migrated to the target domain.
Enable fine-grained password policies to keep existing password policies. Reference: Restructuring Active Directory Domains Within a Forest SID History http://209.85.175.104/search?q=cache:IIJntFlGlVcJ:download.microsoft.com/download/5/2/f/52f23 d76-7d56-44d6-ad25-a95bf0be5516/15_CHAPTER_12_Restructuring_Active_Directory_Domains_Within_a_Forest.doc+re duce+the+number+of+domains+ADMT&hl=en&ct=clnk&cd=10&gl=in
If you want to pass Microsoft 70-647 successfully, donot missing to read latest lead2pass Microsoft 70-647 practice tests.
If you can master all lead2pass questions you will able to pass 100% guaranteed.